US Government Supposes that Malware Attacks from North Korea will Grow






admin
06.07.2018
US Government Supposes that Malware Attacks from North Korea will Grow
 At the recent security summit held in Singapore, Donald Trump and Kim Jong Un friendly-heartedly shook hands. Nevertheless, it is not necessary to assume that everything between the United States and North Korea is so smooth and bright. Just consider this whole situation from the other side, more superficially, and everything will become obvious.
At the recent security summit held in Singapore, Donald Trump and Kim Jong Un friendly-heartedly shook hands. Nevertheless, it is not necessary to assume that everything between the United States and North Korea is so smooth and bright. Just consider this whole situation from the other side, more superficially, and everything will become obvious.
Literally, a couple of days after the signing of the mutual agreement during the negotiations, the US Department of Homeland Security stated that American organizations will be more susceptible to malware from the side of North Korean government.
At the moment it is noted that malware, which is also known as “Typeframe”, has a direct link to cyber-attacks by the hacking gang called Hidden Cobra that is also known as “Guardians of the Peace” or “Lazarus”. A special emphasis of this gang is traced in the imposition of spyware keyloggers, RATs (remote access Trojans), data-wiping malware and attacks of DDoS botnets during hackings of foreign organizations.
Recently, there was news that the system of Chile’s second-largest bank, at the end of May this year, was attacked, as a result of which the bank was inflicted with harmful damage, negatively affecting its services.
Hackers used disk-wiping malware, which belonged to the Hidden Cobra gang so that all attention was drawn to that attack. At the same time, approximately 10 million US dollars were withdrawn through the SWIFT money transfer system.
Thus, if North Korea really were behind these hacking, then the attacks on SWIFT, which resulted in the disappearance of hundreds of millions of US dollars, would have already stopped.
There was already a case when Hidden Cobra was charged with the worldwide sensational WannaCry attack by the US government. As it was obvious, North Korea denied all charges.
The Department of Homeland Security’s US Computer Emergency Readiness Team (US-CERT) did not disclose what exact number of computers have been suffered from Typeframe and which industries may have been most at risk, in its recent report. Despite this, it has analyzed eleven malware patterns, including Microsoft Word document and Windows executables files, which try to install the spyware through the management servers. In turn, this helps to use someone else’s firewalls in order to conduct inbound connections.
It seems that all patterns of malware were assembled sooner than the Singapore Security Summit was made public. To avoid potential hacking and to be as safe as possible from attacks, US-CERT advises the organizations to employ various network signatures and host-based rules, as well as trace network logs for IP addresses.

09 July 2018
0
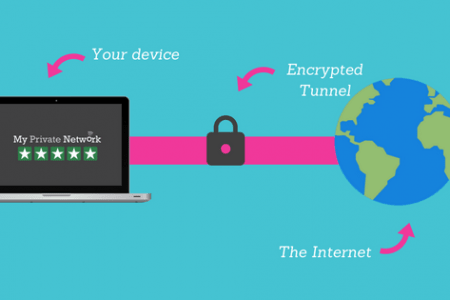
During an Internet session, each person encountered such a nuisance […]
05 May 2018
0
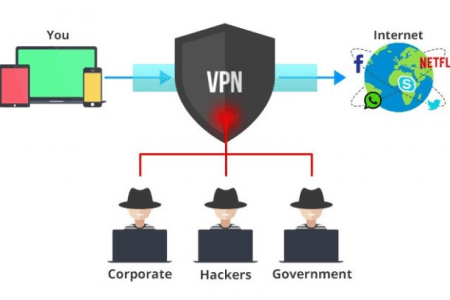
With the rising wave of technologies and development around the […]