How to use VPN






admin
20.04.2018
How to use VPN
Before you get on the board with the use of VPN, you should consider downloading a VPN service of your preference, and set it up on your windows. Certain VPNs are equipped with three-tiers, and each tier is upgraded further on the basis of your usage, and you are required to pay to upgrade to the next tier of a virtual network. A majority of the VPNs makes a claim to return your money if the VPN does not work in your favor.
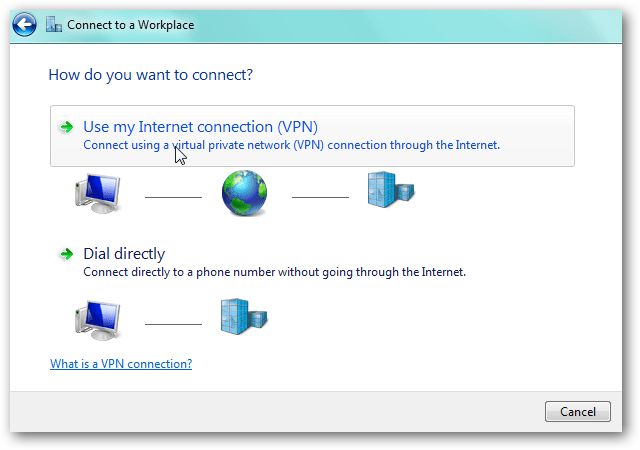
How to use a VPN by following the given simple 5 steps:
- Step 1. Connect to a stable internet: you are simply required to turn on your computer to connect to the internet. Make sure that the windows of your computer are upgraded to meet the requirements of your preferred VPN. If you are in a public place, you will be manually required to establish an internet connection on your computer.
- Step 2. Choose between a free VPN and a paid VPN: VPN can be accessed for free of any cost or, you can pay a significant amount to access the websites via a VPN service. Before you proceed further, you should be clear regarding your preference. It is always better to opt for a service that offers a free trial for a limited time period, and once you are content with the service, you can pay for it.
- Step 3. Launch the VPN software: after downloading and installing the VPN of your choice, you can launch it by following simple instructions. You can locate the VPN software on your windows by employing the Taskbar and the Applications folder. You can also download VPN software that caters to a Mac or Android device.
- Step 4. Carefully read and implement the instructions: several VPNs are relatively easier to start, and they do not require you to read instructions or Terms and Conditions to get started. However, if you have downloaded a VPN like TunnelBear, you will be required to agree to the T&Cs and set up an account to access the software. You can also modify the options that tailor to your preferences the best.
- Step 5. Run and use your VPN: once you have successfully signed up and logged in, you can simply start using your VPN to access the website of your choice. You can also use the VPN to spoof your physical location to protect your identity.
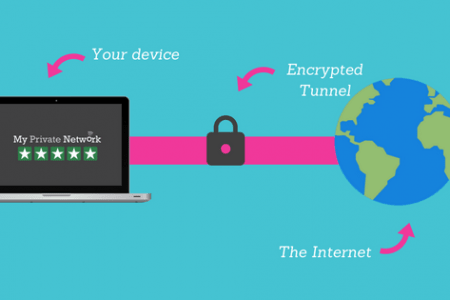
How does the VPN process work?
Connecting to VPN is rather a simple process; however, you might be required to pay for the service depending on the network that you use. Connecting to the internet initially requires you to establish a connection to your Internet Service Provider (ISP), which acts as a gateway to a prohibited internet resource or a website that you intend to access.
In the meanwhile, the internet will collect and establish traffic across the ISP servers, and it could be navigated using the ISP service. Once you have established a connection to a VPN, you will be connected to a server that is controlled by a VPN service or a VPN provider using an encrypted connection, which is termed as the VPN tunnel. The circulation of correlations entails that the exchange of data between the VPN server and your computer is secured and accessed by the authorized parties, which includes you and the server. Once the establishment of the Virtual Private Network is clear to you, you have to keep the following salient features in mind:
1. Your ISP becomes oblivious to your browsing activity
Once you have established an association with a VPN, your ISP will no longer monitor your browsing activity and history. The encryption of the data enables it to keep track on your internet browsing activities, and it becomes oblivious to your search history and internet usage, as the internet activity is running and operated using the VPN server. However, your IPN can only detect that it is connected to a VPN server.
2. Your internet activities are controlled by the IP address assigned to the VPN Server:
If a VPN server is located in an entirely different country in a dissimilar continent, then you have secured better chances in establishing a better and stable connection with the concerned VPN. It will also level-up internet security to an extent. If your internet activity is being monitored from a distance, the chances are that they will be directed to the location of the VPN server. If a VPN provider supplies you with comprehensive and additional details, your true IP address will stay unseen.
3. It makes the public Wi-Fi hotspots safer to use:
If you are connected to a VPN via a public Wi-Fi hotspot, you no longer remain liable to take security and safety measures when using VPN, as the internet connection between the server and your device is encrypted. Given the circumstances, if a malicious and illicit act manages to intercept your data, your data would not be harmed due the occurrence of an encrypted data.
Deployment of security protocols:
Also, apart from the process of VPN, certain security protocols are deployed to a particular VPN to assign a stipulated level of security and features to the private network. Few of this security protocol include:
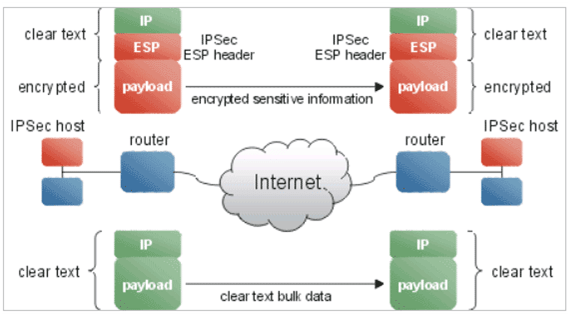
IP Security (IPSec):
The protocol of IPSec is utilized to encrypt the internet communications, and it is employed in two modes; tunneling mode and transport mode. The occurrence of the transport mode merely secures a specific section of the data packet, and the tunneling mode encrypts an intact data packet in comparison. The flexibility and adaptability of the IPSec protocol are used systematically with other protocols to capitalize on enhanced levels of security.
Layer-2 Tunneling Protocol (L2TP)/IPSec:
The IPSec protocol is generally combined with the L2TP protocol to yield a highly secured and feasible VPN patron. This protocol does not play a role in the encryption of the data and connection; however, it induces a tunnel which is further encrypted by the IPSec protocol along with the data integrity checks and channel security to make sure that the data is consistent and congruent.
Transport Layer Security (TLS) / Secure Sockets Layer (SSL):
These two protocols are comprehensively adopted by online retailers and service providers on an online platform. The SSL and TSL protocols are operated via a handshake method, which results in the deployment of a URL that starts with an https:// rather than an http://.
The trend of using VPN (virtual private network) has become a prevalent movement over the years. The technology of the virtual private network was initially introduced to private firms and executives to transfer and access confidential documents in remote privacy. Due to its widespread recognition, it has acquired notoriety amongst the general users of the internet. A VPN also vouches for the commercial VPN services that are inclusive of permitting the customers to access a website remotely using a server. Its use has grown significantly over the years, and it has become a go-to solution to access a prohibited website.
The Virtual Private Networks provides access to a private network to its users, and it results in the sharing of the data confidentially and remotely using public networks. The process and concept of a VPN are fairly analogous to a firewall, which protects the data in a computer, and the employment of the VPN secures the data on the internet. In other words, VPN is a derivative of WAN (Wide Area Network), and it bears the same features and characteristics assigned to a WAN.
For this particular rationale, VPNs are widely used to access websites that are restricted in their current geographical location; it is preferred by corporations to execute the evaluation and management of sensitive data when reaching out to confidential and remote data centers. The use of VPN has also acquired popularity among the regular internet users to access websites that include Netflix, YouTube, Kodi, Torrent, and the websites that are generally prohibited or disabled in a country.
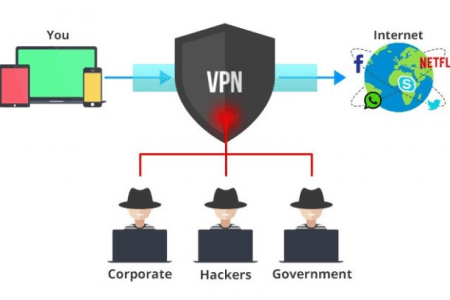
As the VPNs are assigned an amalgamation of connections and encryption protocols to include a virtual and temporary P2P connection, it makes the hacker incapable of monitoring the transfer and nature of the data—which is carried out under an encrypted and secured data. In addition, using VPNs enable the user to spoof their availability on the internet. As the IP address of the user is interchanged by the IP address of the VPN provider—it enables them to bypass content filters.
If you are inclined to connect to the internet via a VPN bridge, it makes you obligated to access a private or a highly-encrypted account or network remotely. Connecting to a VPN is considerably easy and straightforward, as it initially establishes a connection between a user and public internet via an ISP, which is further connected to a VPN server utilizing the software of the concerned client. Once you have initiated the motion of connection, the client software controlling the server will establish a secure connection, which would allow the user to gain access to the internet.

09 July 2018
0
During an Internet session, each person encountered such a nuisance […]
05 May 2018
0
With the rising wave of technologies and development around the […]