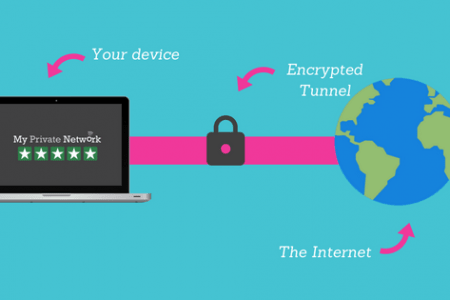
How does a VPN work






admin
05.05.2018
How does a VPN work
With the rising wave of technologies and development around the globe, internet use has become quite reliable and unavoidable. It seems as though the modern world is entirely dependent on this technology, whether at home, at school, at the workplace or on the road, you will find a huge number of people using the internet. Social media, for example, is the biggest platform for internet use where you can find information about any person in the world. Unfortunately, it is the same place where most cybercriminals hunt for their victims. VPN servers come in to help users hide their identities and locations so that you are safe as well as anonymous as you enjoy internet use. This is the same for cooperates and companies that store sensitive information on the internet.
How does VPN work?
A virtual private network is created through the establishment of a virtual point-to-point connection by employing the uses of dedicated connections, virtual tunneling protocols, and most importantly traffic encryption. A VPN can provide many benefits when using extensive area network since the resources in a private network can be accessed remotely.
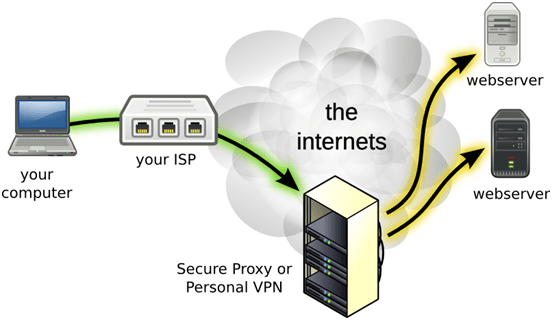
Traditionally, VPNs are characterized by point-to-point topology which in most cases does not support to broadcast domains.
Before understanding how they work, it is important to know why they were created in the first place. Many people may not be aware that virtual private networks were created originally for large organizations so that employees could be able to connect to one computer in one office location while they are out in the field maybe working from the field.
It may not be very easy to understand this, so it’s better if you created a scenario that explains in simplicity. For instance, you know one company that has an office, say in New Delhi, India. The cables and computers in this office are secure and make it hard for hackers to attack because they are in one physical location and they will have to go there to access them. This is called private network.
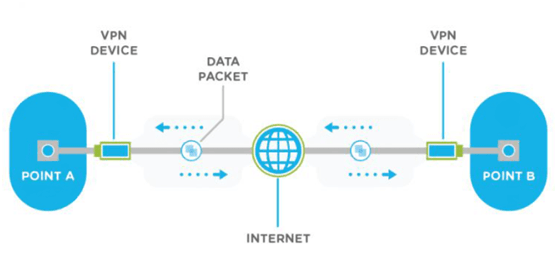
But what if the same company has another office say in South Africa; employees in SA might want to access the private network in New Delhi. It is practically impossible to run a cable to connect these two locations; instead, the company will create its virtual private network which is like a virtual cable.
This is simply how VPNs traditionally came into being to give secure connections to employees of big corporations and business helping them access important files from different locations without posing a risk to security.
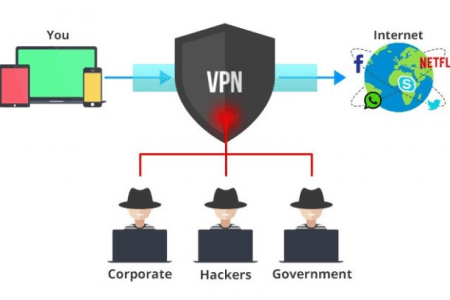
Now that you know, how it began, let’s try to understand how it works. As seen above, after creating the virtual cable, it becomes essentially a virtual tunnel that encrypts data as it passes through it. Anyone with, intentions of prying on the data, like governments, ISPs, hackers or anyone with intentions of accessing the data without proper access will not be able to do so.
The tunnels are created by first authenticating your client, say an android phone or a laptop with a VPN server, which you can run yourself with special programs such as Kodi. The server then uses one of several other options protocols which make everything you sent between you, the website and internet service provider impossible to monitor the ring. It is like the information you share is wrapped into a box, which no one else can be able to open and view but you.
To better understand this, we can discuss how it works through the VPNs three main components.
- Protocols( security)
VPNs are characterized by security protocols that protect information that passes through is by creating secure connections as well as influence the type of encryption used by the VPN. Here are the most widespread protocols:
- IP security: IP security, commonly known as IPsec is common to secure internet communications and operates in two modes, transport mode that encrypts the data packet message only and the tunneling mode that encrypts the entire data packet.
- Level 2 Tunneling Protocol (L2TP)/IPsec: These protocols combine their best features to create a very high secure client. L2TP is unable to encrypt, it only generates a tunnel while the IPsec protocol takes care of encryption, channel security and checks data integrity to ensure they are not compromised.
- Secure Sockets Layer (SSL) and Transport Layer Security (TLS): These two are used more in the security of online retailers and services providers by using handshake method. A handshake is performed at the beginning of every SSL session to produce cryptographic parameters of the sessions, typically digital certificates, which are the means by authentication is achieved.
- Point-to-point Tunneling Protocol (PPTP): Though it has been used since the mid-1990s and can be installed on many OSs. However, just like L2TP, it does not encrypt bur rather tunnels and encapsulates the data packet. A secondary protocol is used to handle encryption.
- Secure Shell: SSH simply creates both VPN tunnel and the encryption to protect it allowing users to transfer data via a router that takes the traffic through from remote servers through an encrypted channel. Note that the data is secure and not encrypted, but the channel is. The SSH is created by a specific SSH client. After creating, the client will forward the traffic from a local port or location on the remoter server. The ports are very specific, and data between the two ends flows through them.
- Encryption
Encryption simply works together with security; it protects the data by encrypting it. Finding the best VPN can be done through understanding the encryption protocol, the best use AES (Advanced Encryption Protocol) 128-bit and 256-bit. VPNs are defined by encryption, meaning it is the most important feature.
- Servers
The selling point of many VPNs is the number of servers they have. The more the number of servers it has, the better the VPN is. Servers are simply branches in different locations. Proximity matters a lot in the use of VPNs.
What is a VPN
Any internet user who does not know about VPN use could still be living in the analog era. Anyways, the virtual private network can be defined easily through its use. It is an amazing connectivity tool that can give you access to blocked websites; it can hide your location, it can encrypt your data and hide your logs among many other awesome features.
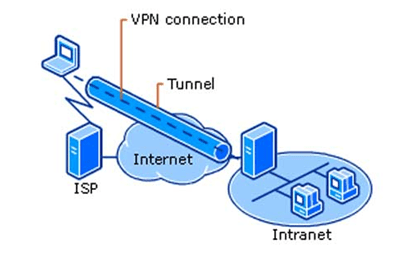
It extends private networks on a public network by enabling users to share data across shared or public networks, like public Wi-Fi and so on, by making their computing devices (phones, tablets, computers, etc.) to seem as though they are connected to the private network.
Through virtual private networks, employees can access cooperate intranet securely even when they are outside the office. VPNs create a cohesive network for cooperates by securely connecting offices of the same organization located in different places.
Apart from organizations, individual users also need VPN app to work around blocked websites as well as bypass censorship. In simple terms, you can be able to view restricted websites in your country without any problem. Each country has its laws regarding the type of information that can be accessed in that particular country and the websites that are allowed. If you wanted to access this information, you could do so through virtual private networks.
Despite this though, there are many internet sites that block access to some familiar VPN technology to try and protect their geo-restrictions from being broken. But this has never stopped these connections because many personal use VPN providers have come up with better technologies to bypass blocking proxies.
Why do you need VPN?
Here are reasons you will need to use VPN app.
· Bypass censorship
There is a lot of censorship on the internet today, and many firewalls are impossible to bypass. Using VPN gives you easily jump over these firewalls.
· Downloading files and streaming
BitTorrent is software that allows users to download files which can be useful. Sometimes this is not legal though. Streaming channels like Netflix also have their own rules concerning the use. For faster streaming and downloading, especially over a public network, you don’t want to miss on VPN.
-
When accessing geo-blocked websites
Some websites are specific to the certain region. Netflix, for example, may have an account that can only be used while in America, which is impossible to use when roaming. VPN helps you bypass these restrictions by connecting using VPNs located in the USA even if you in China or in other countries.
· Other Uses
You will also need VPN when accessing a business or home network while traveling. Most importantly, you need VPN services to hide your browsing activities from your local network and ISP especially if you are using a public network.
Tags:

09 July 2018
0
During an Internet session, each person encountered such a nuisance […]
05 May 2018
0
With the rising wave of technologies and development around the […]